InfoSec CTF – VaultBox
VaultBox is a "secure vault" app that claims to store passwords, files, and images. At first glance, it looks like a normal vault manager… but something feels off.
VaultBox Forensics Write-up
Category: Forensics
Prompt: VaultBox is a “secure vault” app that claims to store passwords, files, and images. At first glance, it looks like a normal vault manager… but something feels off.
Artifact: ⬇️ app-debug.apk
Flag format: FlagY{…}
Intro
VaultBox looks clean and “secure” but the whole thing felt staged. I treated it like a prop vault: open it up, poke the lining, and see what falls out.
Challenge Description
Given an Android APK . The goal: find the flag hidden somewhere inside the app package.
Steps
1) I opened the APK directly in JADX .
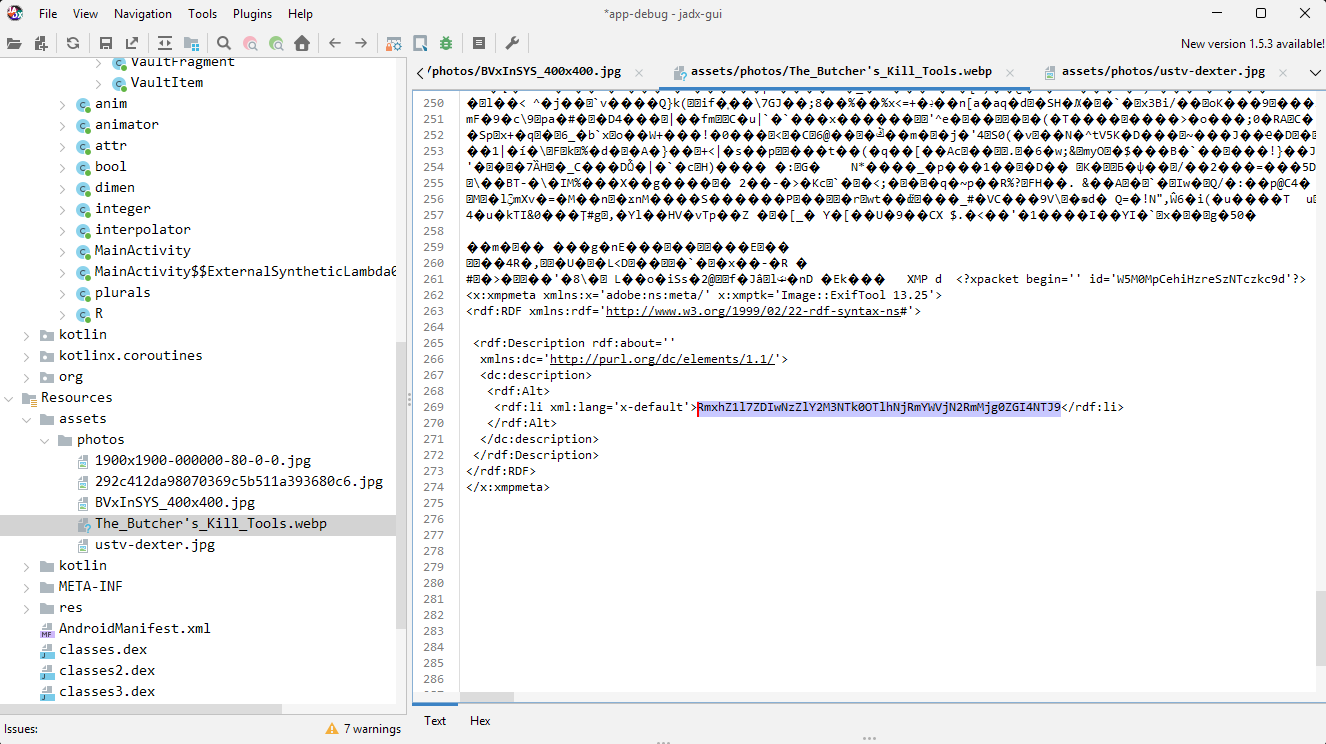
2) From the left tree, I jumped straight to the Resources → assets → photos folder.
3) One file stood out: assets/photos/The_Butcher’s_Kill_Tools.webp.
4) In the XMP block , there was a Base64 string starting with RmxhZ1l7, which is a giveaway for FlagY{.
5) The full blob: RmxhZ1l7ZDIwNzZlY2M3NTk0OTlhNjRmYWVjN2RmMjg0ZGI4NTJ9
6) Decoding it gives the flag.
Output:
1
FlagY{d2076ecc759499a64faec7df284db852}